The Methods to Access EC2 : SSH, EC2 Instance Connect, System Manager
Overview
While there are lots of third partys tool can let user to configure servers, you occasionally must access your instances to fine-tune, consult system logs, or debug application issues …etc.
AWS support many ways to let you connect to your servers(EC2), we will introduce three methods : SSH, Instance Connect, System Manager and deep dive in EC2 Instance Connect and System Manager – Session Manager.
SSH connection
The most common tool to connect to Linux servers is Secure Shell (SSH). It was created in 1995 and is now installed by default on almost every Linux distribution.
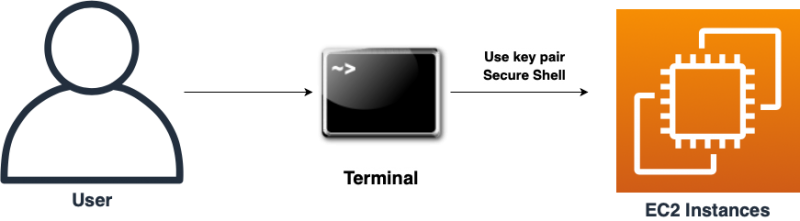
How to Configure
After you launch your instance, you can connect to it and use it the way that you’d use a computer sitting in front of you. When you want to SSH to EC2 instance, make sure the configuration is well.
Before you connect to your instance, complete the following prerequisites :
-
Verify the general prerequisites for connecting to your instance :
- Get information about your instance
- Enable Inbound traffic
- Locate the private key and verify permissions
-
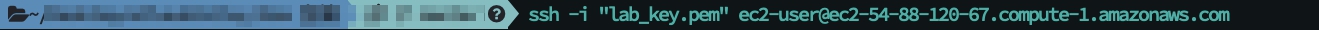
In a terminal window, use the ssh command to connect to the instance.
- Make sure you are enter the right location of your key.
ssh -i /path/my-key-pair.pem ec2-user@ec2-xx-xx-xx-xx.compute-1.amazonaws.com
-
(IPv6 only) Alternatively, you can connect to the instance using its IPv6 address.
ssh -i /path/my-key-pair.pem ec2-user@2001:db8:1234:1a00:9691:9503:25ad:1761 -
You see a response like the following:
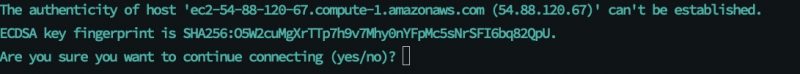
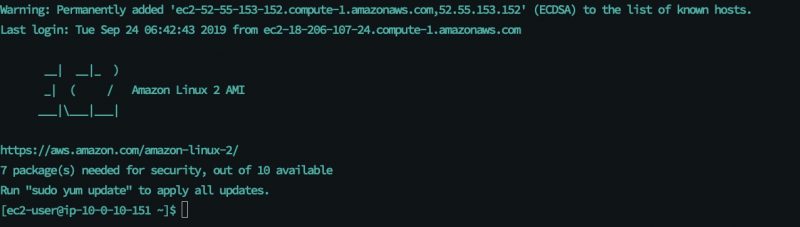
- Enter
yes. You are connect to your instance !
EC2 Instance Connect
AWS in JUN 27 2019 update the new feature of EC2 SSH connection, EC2 Connect. A new way to control SSH access to your EC2 instances using Identity and Access Management (IAM).
The following Linux distributions are supported:
-
Amazon Linux 2 (any version)
-
Ubuntu 16.04 or later

How to Configure
-
Verify the general prerequisites for connecting to your instance using SSH.
- Get information about your instance
- Locate the private key and verify permissions
-
Enable Inbound traffic
Ensure that the security group associated with your instance allows inbound SSH traffic on port 22 from your IP address.
-
At first time, we need to install the Instance Connect on the instance. This is a one-time requirement for each instance.
Amazon Linux 2 2.0.20190618 or later comes preconfigured with EC2 Instance Connect. For other supported Linux distributions, you must set up Instance Connect for every instance that will support using Instance Connect.
Notes : If you configured the
AuthorizedKeysCommandandAuthorizedKeysCommandUsersettings for SSH authentication, the EC2 Instance Connect installation will not update them. As a result, you cannot use Instance Connect. -
(Optional) Install the EC2 Instance Connect CLI.
pip install ec2instanceconnectcliThe EC2 Instance Connect CLI provides a similar interface to standard SSH calls, which includes querying EC2 instance information, generating and publishing ephemeral public keys, and establishing an SSH connection through a single command.
-
Connect to your instance using SSH.
-
Install the EC2 Instance Connect package on your instance.
-
For Amazon Linux 2, use the yum install command.
sudo yum install ec2-instance-connect -
For Ubuntu, use the sudo apt-get command to install the .deb package
sudo apt-get install ec2-instance-connect
-
-
Configure IAM policy for EC2 Instance Connect
For your IAM users to connect to an instance using EC2 Instance Connect, you must grant them permission to push the public key to the instance.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2-instance-connect:SendSSHPublicKey"
],
"Resource": [
"arn:aws:ec2:Your-Region-1:ACCOUNTID:instance/*"
],
"Condition": {
"StringEquals": {
"ec2:osuser": "ec2-user"
}
}
}
]
}
You need to modify the Your-Region-1 and ACCOUNTID in the policy.
-
Attach the policy to IAM Group or IAM User.
Restrict the permissions to the specific user or group.
-
Navigate to the EC2 instance Console, select Connect.
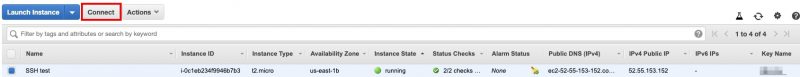
- Select EC2 Instance Connect, and then Connect.
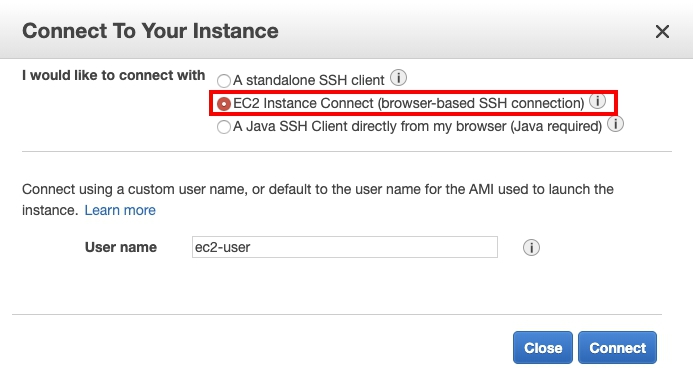
- Now you can use the browser-based SSH connect to your instance.
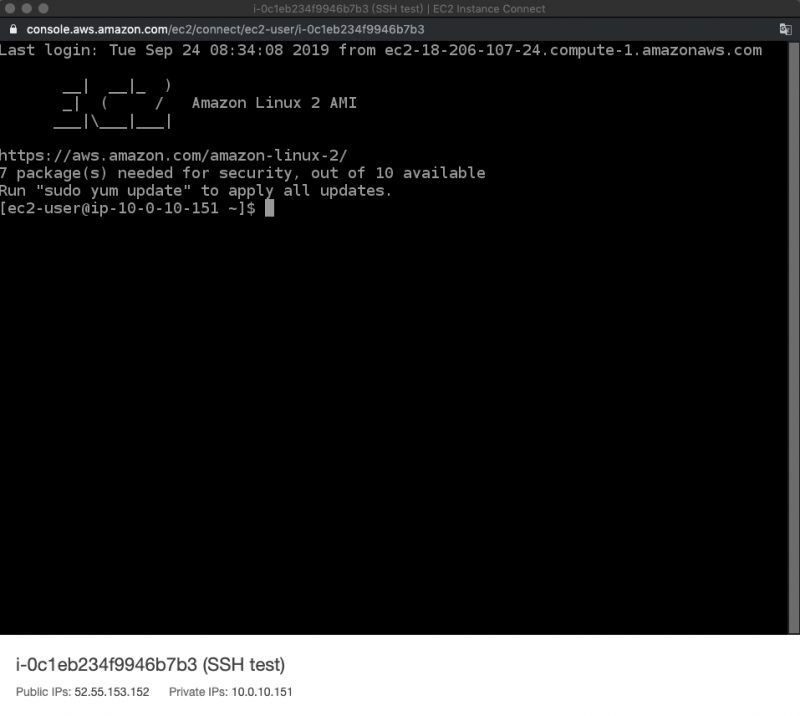
-
(Optional)You also can connect to an instance using the EC2 Instance Connect CLI by providing only the instance ID.
mssh i-003234a4bf40dec41EXAMPLEThe Instance Connect CLI performs the following three actions in one call : it generates a one-time-use SSH public key, pushes the key to the instance where it remains for 60 seconds, and connects the user to the instance. You can use basic SSH/SFTP commands with the Instance Connect CLI.
How It Works
-
Generate a public / private key pair on the client.
-
Register the public key with EC2 Instance Connect API (SendSSHPublicKey).
-
EC2 Instance Connect saves the public key in Instance Metadata of the target EC2 for 60 seconds.
-
EC2 Instance Connect agent on EC2 obtains public key from Instance Metadata and registers with sshd.
-
Log in to EC2 using SSH from the client with SSH.
-
User can find the audit logs in CloudTrail.
System Manager – Session Manager
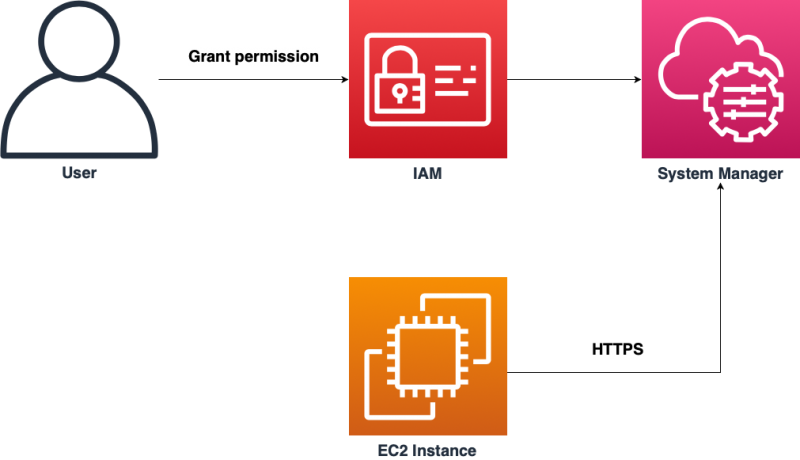
AWS System Manager – Session Manager is a fully managed AWS System Manager capability that lets you manage your Amazon EC2 instances through an interactive one-click browser-based shell or through the AWS CLI.
The following Linux distributions are supported:
-
Amazon Linux 2、Linux
-
Ubuntu 18.04、16.04
-
Windows Server 2008 R2 through Windows Server 2016
-
On-premises server and virtual machines for your hybrid environment__
__You need to install the agent manually
How to Configure
-
Install the AWS Systems Manager agent on each EC2 instance (already installed on Amazon Linux).
-
Create an IAM role for the EC2 instance which grants access to the AWS Systems Manager.
You can attach the built-in policy, AmazonSSMManagedInstanceCore to a role.
-
Attach the role to your instance.
-
Use the Session Manager console to connect to your server.
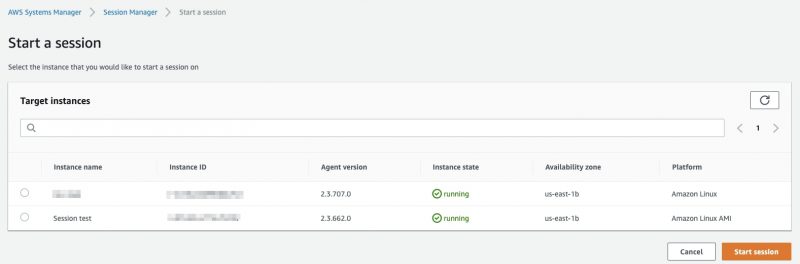
- You have already connected to your server.
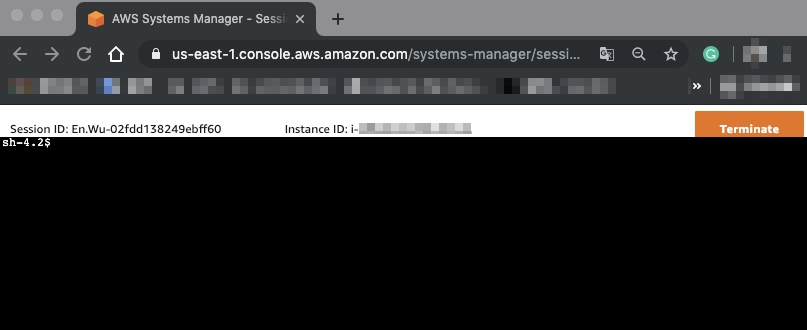
How It Works
-
Authenticates against IAM (IAM user or SSO identity provider).
-
IAM authorizes to start a session for an EC2 instance (IAM policy).
-
The user uses the AWS Management Console or the terminal (AWS CLI and additional plugin required) to start a session via the Systems Manager.
-
An agent running on the EC2 instance connects to the Systems Manager’s backend and executes commands on the machine.
The EC2 instance needs access to the Internet or a VPC endpoint.
-
The Session Manager sends audit logs to CloudWatch Logs or S3.
Summary
When connecting to hosts via SSH, SSH key pairs are often used to individually authorize users. As a result, organizations have to store, share, manage access for different users, and maintain these SSH keys.
Some organizations also maintain bastion hosts, which help limit network access into hosts by the use of a single jump point. They provide logging and prevent rogue SSH access by adding an additional layer of network obfuscation. However, running bastion hosts comes with challenges. You maintain the installed user keys, handle rotation, and make sure that the bastion host is always available and, more importantly, secured.
EC2 Instance Connect offers an alternative to complicated SSH key management strategies. By integrating with IAM and the EC2 instance metadata available on all EC2 instances, you get a secure way to distribute short-lived keys and control access by IAM policy, it means you replace the key with the IAM policy.
BTW, if EC2 Instance Connect has been used recently, you should see records of your users having called this API operation to send their SSH key to the target host in CloudTrail. Viewing the event’s details shows you the instance and other valuable information that you might want to use for auditing.
But there are some limitation of EC2 Instance Connect like AMI type, public IP and Inbound port… etc.
In addition to not requiring you to open inbound ports, you can use Session Manager with AWS PrivateLink to prevent traffic from going through the public internet. Session Manager also support the on-premises server, all you need to do is install the SSM agent.
Compare EC2 Instance Connect with Session Manager :
-
Similar :
-
They all use IAM policy to grant permession instead of Key.
-
No need of a bastion server or the SSH key. (Instance Connect is use SSH)
-
They all provide a convenient way for audit mechanism.
Instnace Connect : CloudTrail
Session Manager : CloudTrail, CloudWatch Logs
-
-
Different :
-
Instance Connect basically requires public IP and network connectivity. However, Session Manager can also connect to a private subnet via PrivateLink (or NAT Gateway).
See Use PrivateLink to Set Up a VPC Endpoint for Session Manager
-
Instance Connect is use SSH to connect to server ; Session Manager is use HTTPS.
You should configure the network inbound and outbound depends on different methods.
-




